What Is Microsofts Best Practice When It Comes to Creating Additional Active Directory Domains?
This is the about comprehensive list of DNS best practices and tips on the planet.
In this guide, I'll share my best practices for DNS security, blueprint, performance, and much more than.
Table of contents:
- Take at least Two Internal DNS servers
- Use Agile Directory Integrated Zones
- Best DNS Order on Domain Controllers
- Domain-joined Computers Should Only Use Internal DNS Servers
- Point Clients to The Closest DNS Server
- Configure Aging and Scavenging of DNS records
- Setup PTR Records
- Root Hints vs Forwarding (Which one is the best)
- Enable Debug Logging
- Utilize CNAME Records for Alias (Instead of A Record)
- DNS Best Practice Analyzer
- Basic: DNS Security Tips
Alarm: I practise not recommend making changes to critical services similar DNS without testing and getting approval from your system. You should be following a change management process for these types of changes.
Have at least Ii Internal DNS servers
In small to large environments, you should have at least two DNS servers for redundancy. DNS and Active Directory are disquisitional services, if they neglect you volition accept major problems. Having two servers will ensure DNS volition notwithstanding function if the other one fails.
In an Active Directory domain, everything relies on DNS to function correctly. Even browsing the net and accessing cloud applications relies on DNS.
I've experienced a complete domain controller/DNS failure and I'm not joking when I say most everything stopped working.
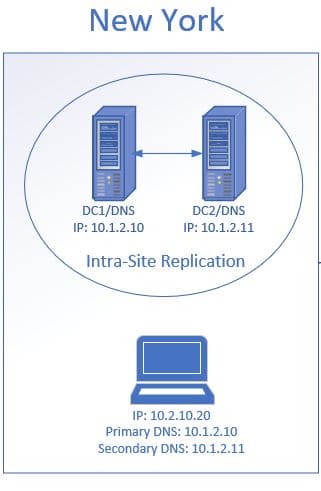
In the above diagram, my site has two domain controllers and DNS servers. The clients are configured to use DHCP, the DHCP server will automatically configure the client with a master and secondary DNS server. If DC1/DNS goes downwards the client will automatically apply its secondary DNS to resolve hostnames. If DC1 went down and at that place was no internal secondary DNS, the customer would be unable to access resources such every bit electronic mail, apps, internet, and so on.
Bottom line: Ensure you have back-up in place by having multiple DNS/Agile Directory servers.
Recommended Tool: SolarWinds IP Accost Manager
IP Address Manager (IPAM) can provide y'all with centralized IP address management and tracking. Centralize DNS, DHCP, and IP management into a single web console. Works with Microsoft, Cisco, and BIND DNS Servers.
Try it Gratuitous
Use Active Directory Integrated Zones
To make the deployment of multiple DNS servers easier you should use Active Directory integrated zones. You can only apply AD integrated zones if you have DNS configured on your domain controllers.
Advertisement integrated zones have the following advantages:
- Replication: AD integrated zones store data in the AD database every bit container objects. This allows for the zone information to get automatically replicated to other domain controllers. The zone information is compressed allowing data to be replicated fast and deeply to other servers.
- Redundancy: Becuase the zone information is automatically replicated this prevents a single point of failure for DNS. If one DNS server fails the other server has a full re-create of the DNS information and can resolve names for clients.
- Simplicity: AD Integrated zones automatically update without the demand to configure zone transfers. This simplifies the configuration while ensuring redundancy is in identify.
- Security: If yous enable secure dynamic updates, then only authorized clients can update their records in DNS zones. In a nutshell, this means just members of the DNS domain tin register themselves with the DNS server. The DNS server denies requests from the computers that are not function of the domain.
Best DNS Order on Domain Controllers
I've seen lots of discussion on this topic. What is the best do for DNS order on domain controllers?
If you do a search on your own you volition come across diverse answers BUT the majority recommends the configuration below.
This is also Microsoft's recommendation.
- Primary DNS: set to another DC in the site
- Secondary DNS: Ready to itself using the loopback address
Let's look at a real-globe example.
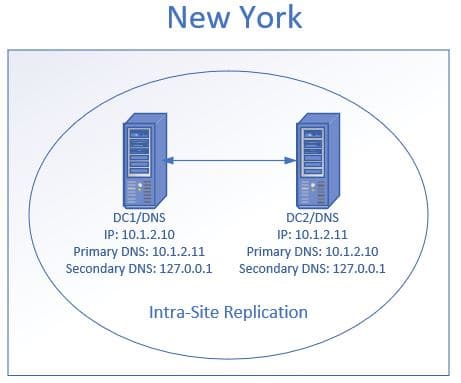
In the above diagram, I have two domain controllers/DNS at the New York site. I accept DC1 primary DNS fix to its replication partner DC2. Then the secondary DNS is set to its self using the loopback address. Then DC2 principal DNS is set to DC1 and its secondary set to itself using the loopback address.
Microsoft claims this configuration improves performance and increases the availability of DNS servers. If you point the chief DNS to itself first it tin can cause delays.
Source: https://technet.microsoft.com/en-us/library/ff807362(5=ws.10).aspx
Domain Joined Computers Should Only Use Internal DNS Servers
Your domain joined computers should have both the chief and secondary DNS ready to an internal DNS server. External DNS servers cannot resolve internal hostnames so this could event in connectivity issues and prevent the computer from accessing internal resources.
Permit'southward look at an instance of why this is a bad setup.
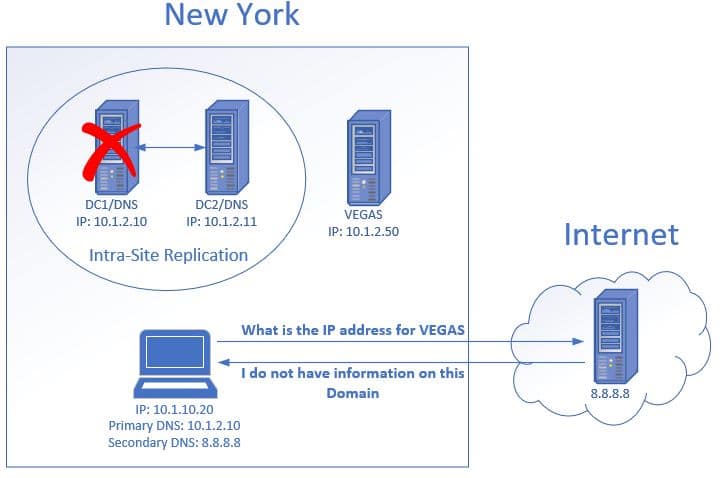
- The client makes a asking to an internal server chosen VEGAS.
- The customer decides to contact its secondary DNS server which is viii.eight.8.eight. It asks the server what the IP address is for the host VEGAS.
- The external DNS knows nothing about this host, therefore, it cannot provide the IP address.
- This results in the client being unable to access the VEGAS file server.
Typically if the chief DNS server is bachelor it will be used first but it may be unresponsive which tin effect in using the secondary DNS. Information technology may take a reboot of the computer for it to switch back to the master DNS, this can result in frustrated users and calls to helpdesk.
The recommended solution is to have 2 internal DNS servers and e'er point clients to them rather than an external server.
Point Clients to the Closest DNS Server
This will minimize traffic across WAN links and provide faster DNS queries to clients.
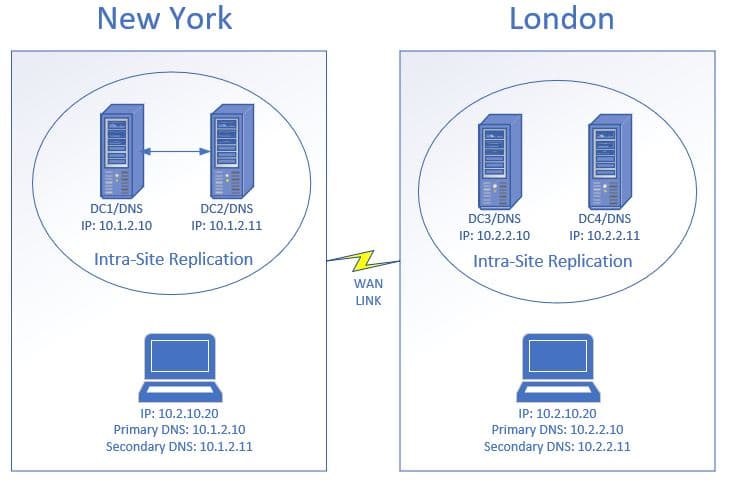
In the diagram above the customer computers are configured to use the DNS servers that are at their site. If the customer in New York was incorrectly configured to use the DNS servers in London this would result in tiresome DNS functioning. This would affect the user's apps, cyberspace access, and so on. I hope yous users will be complaining about how irksome everything is.
The best way to automatically configure the right DNS servers is by using DHCP. You should have different DHCP scopes setup for each site that includes the primary and secondary DNS servers for that site.
Configure Aging and Scavenging of DNS Records
DNS crumbling and scavenging allow for automatic removal of old unused DNS records. This is a two-role process:
Aging: Newly created DNS records get a timestamp practical.
Scavenging: Removes DNS records that have an outdated timestamp based on the time configured.
Why is this needed?
At that place will be times when computers register multiple DNS entries with different IP addresses. This can be caused past computers moving around to dissimilar locations, computers existence re-imaged, computers beingness dropped and added back to the domain.
Having multiple DNS entries will cause name resolution issues which issue in connectivity issues. DNS aging and scavenging volition resolve this past automatically deleting the DNS record that is not in use.
Aging and Scavenging merely apply to DNS resource records that are added dynamically.
Resource:
How to Configure DNS Crumbling and Scavenging (Cleanup Stale DNS Records)
Setup PTR Records for DNS Zones
PTR records resolve an IP address to a hostname. Unless you are running your own mail server PTR records may not be required.
Simply… they are extremely helpful for troubleshooting and increasing security.
Some systems like firewalls, routers, and switches only log an IP address. Accept for instance the windows firewall logs.
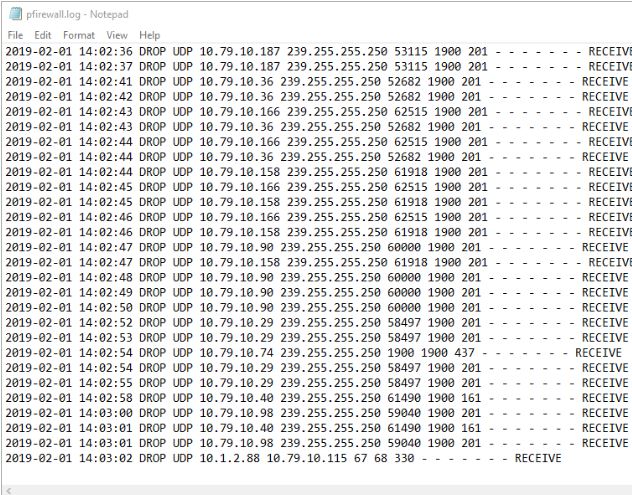
In this example, helpdesk was troubleshooting a printer issue and thought x.one.2.88 was a printer being blocked by the firewall. Because I accept PTR records setup I was able to quickly look it up using the nslookup command.
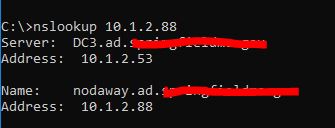
10.one.2.88 resolves to nodaway.ad.activedirectorypro.com, I know this is a server and non a printer. If I didn't have a PTR record setup I would have been digging through inventory trying to find more information about this IP.
There is really no reason not to setup PTR records, it's like shooting fish in a barrel to setup and causes no additional resources on the server. See my consummate guide on setting upwardly reverse lookup zones and ptr records.
Additional Resources:
NSLookup to Cheque DNS Records
Root Hints vs DNS Forwarders (Which i is the best)
Past default, Windows DNS servers are configured to utilize root hint servers for external lookups. Another selection for external lookups is to use forwarders.
Basically, both options are ways to resolve hostnames that your internal servers cannot resolve.
So which one is the all-time?
Through my own feel and research, information technology really comes down to personal preference.
Here are some general guidelines they volition assistance you decide:
- Use root hints if your main concern is reliability (windows default)
- Forwarders might provide faster DNS lookups. You can utilise benchmarking tools to test lookup response times, link included in the resource department.
- Forwarders can also provide security enhancements (more on this below)
- Forwarders must exist configured manually on each DC
For years I used the default setting (root hints) and so I was introduced to Quad9 at a security conference. Quad9 is a free, recursive, anycast DNS platform that provides end users robust security protections, loftier-functioning, and privacy. In a nutshell, Quad9 checks the DNS lookup against a list of bad domains, if the customer makes a request to a domain on the list that request is dropped.
I've used this service for over a twelvemonth now and I've had zilch issues. Since security has been a big concern for me it was my personal preference to switch to Quad9 forwarders from root hints. It is providing fast and reliable lookups with the added bonus of security.
Quad9 does not provide whatever reporting or analytics. The blocked requests are logged in the Windows Server DNS debug logs, so make sure you read the next section on how to enable information technology. The drops will be recorded with NXDomain so you could build a study by looking for that in the logs.
Additional Resources:
OpenDNS – is some other company that offers this service, it has a high cost merely includes additional features and reporting.
How Quad9 Works – This page shows how to setup Quad9 on an individual computer, if you have your own DNS servers DO Not DO THIS. You will want to use your DNS server and add quad9 as a forwarder. This page provides some boosted details and is the master reason why I included information technology. You lot could employ these steps for your home computer or devices that simply need internet access.
DNS Benchmark tool – Gratis tool that allows you to examination the response times of any nameservers. This may aid yous determine if you lot want to stick with root hints or utilise forwarders.
List of Root Servers
Enable DNS Debug Logging
DNS debug logs can be used to runway down problems with DNS queries, updates, and other DNS errors. Information technology can also exist used to runway customer action.
With logging tools like splunk you lot can create reports on top domains, top clients and find potential malicious network traffic.
Microsoft has a log parser tool that generates the output beneath:
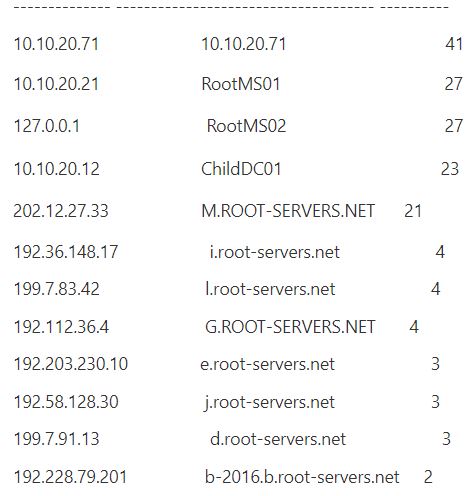
You should be able to pull the debug log into whatsoever logging tool or script to create your own reports.
How to Enable DNS Debug Logs
Step ane: On the DNS panel correct click your DNS server and select properties
Pace 2: Click on the Debug Logging Tab
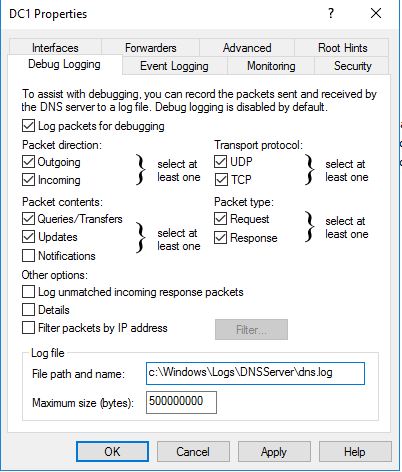
Change the default path and max size, if needed.
Boosted Resources:
Parsing DNS server log to track active clients
Use CNAME Tape for Alias (Instead of A Record)
- A record maps a name to an IP address.
- CNAME record maps a name to another name.
If you use A records to created aliases y'all will end upward with multiple records, over time this volition become a big mess. If you lot have PTR records configured this volition also create additional records in that zone which will add to the mess and create bigger bug.
If you need to create an alias information technology'southward meliorate to utilize CNAME records, this will exist easier to manage and prevent multiple DNS records from being creating.
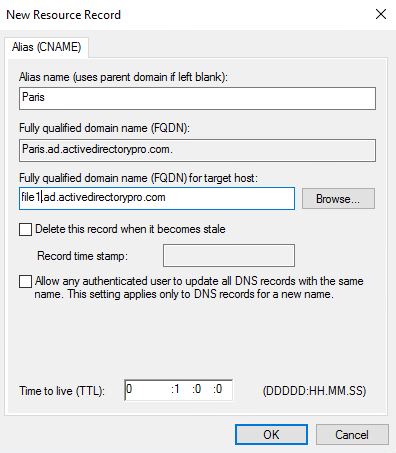
How to Create an Alias CNAME record
I have an A Record setup for my file server called file1 that resolves to IP 192.168.0.201
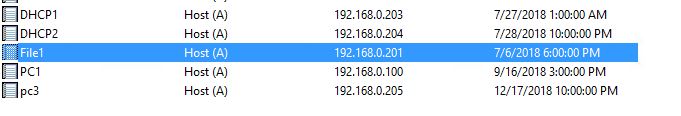
Our Dev team wants to rename the server to Paris to make information technology more user friendly. Instead of re-naming the server I'll just create a CNAME record.
Right click in the zone and click on New Alias (CNAME)
For Alias name, I'll enter Paris
The alias name resolves to file1 then I add that to the target host box:
Click OK and you're done!
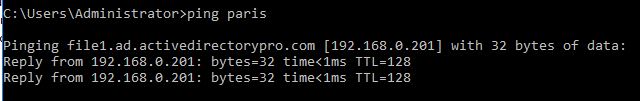
Now I can access Paris by hostname which resolves to file1
Easy Right?
This keeps DNS clean and helps prevent DNS lookup issues.
Use DNS Best Practice Analyzer
The Microsoft best practice analyzer is a tool that scans server roles to check your configuration against Microsoft guidelines. It is a quick way to troubleshoot and spot potential problems configuration bug.
The BPA can be ran using the GUI or PowerShell, instructions for both are below.
How To Run BPA DNS Using The GUI
Open Server Managing director, and so click DNS
Now roll down to the Best Practices Analyzer section, click tasks so select "Start BPA Scan"
Once the scan completes the results volition be displayed.
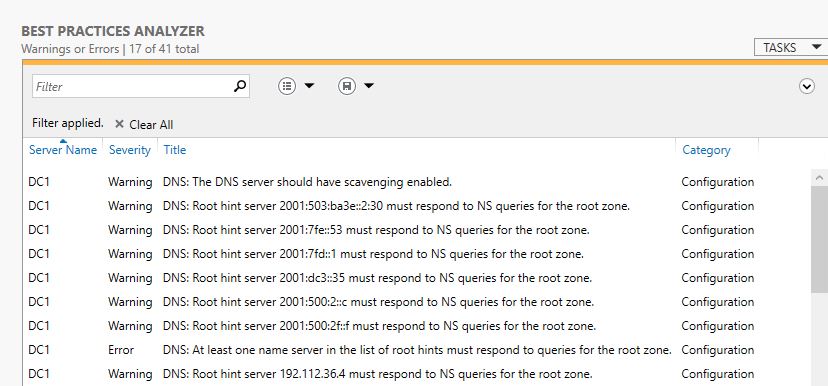
How To Run BPA DNS Using The PowerShell
You will commencement demand the ID of the role. Run this command to get the ID
Become-BPaModel
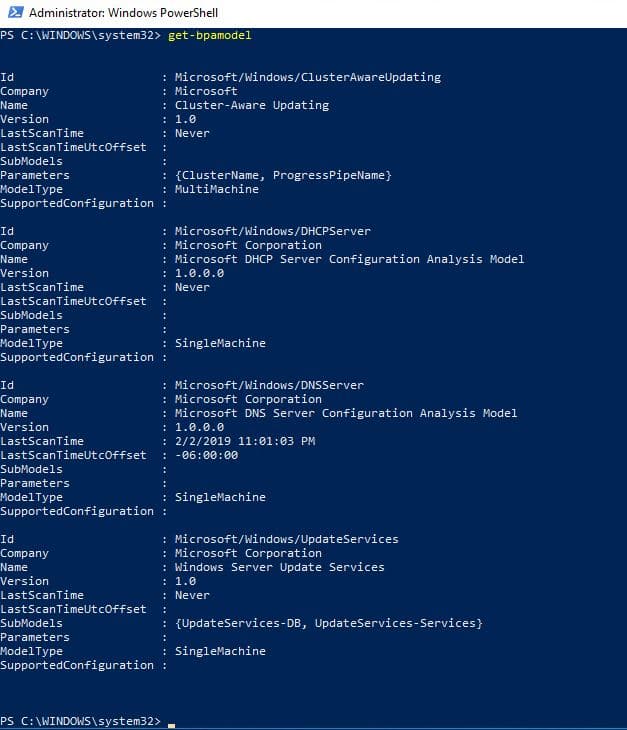
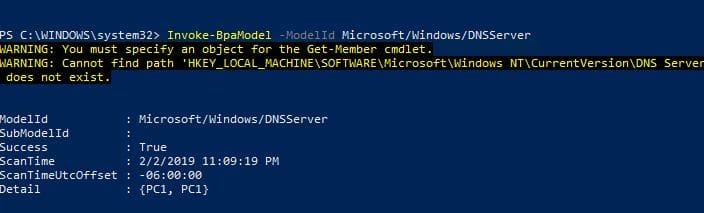
I tin can the ID for DNS is Microsoft/Windows/DNSServer. I take that ID and use this command to run the BPA for DNS.
Invoke-BPAModel "Microsoft/Windows/DNSSerer"
You may go some errors, this is normal
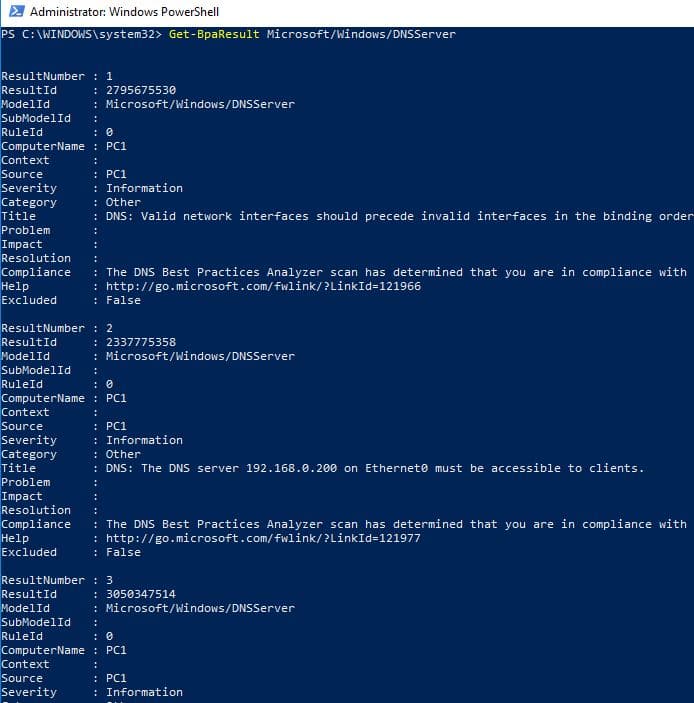
The above command only runs the analyzer it does not automatically display the results.
To brandish the results run this command:
Get-BpaResult Microsoft/Windows/DNSServer
Bonus: DNS Security Tips
I think we tin can all concur that DNS is an important service. How would anything part without? At present let'southward await at a few ways we can secure this service, some of these features are enabled by default on Windows servers.
- Filter DNS Requests (Block Bad Domains)
- Secure DNS forwarders
- DNS Enshroud Locking
- DNS Socket Pool
- DNSSecFilter DNS Requests (Cake bad domains)
Filter DNS Requests (Cake Bad Domains)
One of the best ways to prevent viruses, spyware, and other malicious traffic is to block the traffic before it fifty-fifty hits your network.
This can be done past filtering DNS traffic through a security appliance that checks the domain proper name against a list of bad domains. If the domain is on the list the traffic will be dropped preventing any farther advice between the bad domain and client. This is a mutual feature on side by side generation firewalls, IPS systems (Intrusion Prevention System), and other security appliances.
I've been using a Cisco FirePower firewall that provides this service. Cisco provides a feed (list of bad domains) that is automatically updated on a regular basis. In addition, I tin can add together additional feeds or manually add together bad domains to the list. I've seen a huge decrease in viruses and ransomware type threats since I've been filtering DNS requests. I've been amazed at how much bad traffic this detects and blocks, surprisingly very little false positives!
Boosted Resource:
Cisco Side by side Generation Firewall official site
https://www.cisco.com/c/en/us/products/security/firewalls/index.html
Paloalto – Another pop firewall/IPS organisation
https://www.paloaltonetworks.com/products/secure-the-network/next-generation-firewall
Secure DNS Forwarders
Secure DNS forwarders are some other way to filter and block DNS queries.
In add-on to blocking malicious domains, some forwarding services offering web content filtering. This allows you lot to cake requests based on a category like adult content, games, drugs and then on. One big reward this has over an on-premise apparatus like a firewall is this can provide protection to devices when they are off the network. Information technology may require a client be installed on the device but it would direct all DNS traffic through the secure DNS forwarder if the device was on the internal or external network.
List of DNS Forwarding Filters:
Quad9
OpenDNS
DNSFilter
DNS Cache Locking
DNS cache locking allows yous to control when the DNS cache can exist overwritten.
When a DNS server performs a lookup for a client, it stores that lookup in the cache for a period of fourth dimension. This allows the DNS server to answer faster to the same lookups at a later time. If I went to espn.com the DNS server would cache that lookup, so if anyone went to it at a later time it would already be buried assuasive for a faster lookup.
1 type of set on is poising the cache lookup with false records. For example, we have espn.com in the enshroud, an attacker could alter this record to redirect to a malicious site. The adjacent time someone went to espn.com information technology would send them to the malicious site.
DNS enshroud locking blocks records in the cache from being changed. Windows Server 2016 has this featured turn on by default.
Boosted Resource
DNS Socket Pool
DNS Socket puddle allows the DNS server to apply source port randomization for DNS lookups. By using randomized ports the DNS server will randomly pick a source port from a pool of bachelor sockets. Instead of using the aforementioned port over and over information technology volition choice a random port from the pool, this makes information technology hard for the attacker to estimate the source port of a DNS query.
This is also enabled by default on Windows server 2016
Additional Resources
Microsoft Configure the Socket Pool
DNSSEC
DNSSEC adds a layer of security that allows the client to validate the DNS response. This validation procedure helps prevent DNS spoofing and cache poising.
DNSSec works past using digital signatures to validate the responses are authentic. When a client performs a DNS query the DNS server will attach a digital signature to the response, this allows the client to validate the response and prove information technology was not tampered with.
Boosted Resources:
Overview of DNSSec
Pace by Step implementation
Source: https://activedirectorypro.com/dns-best-practices/